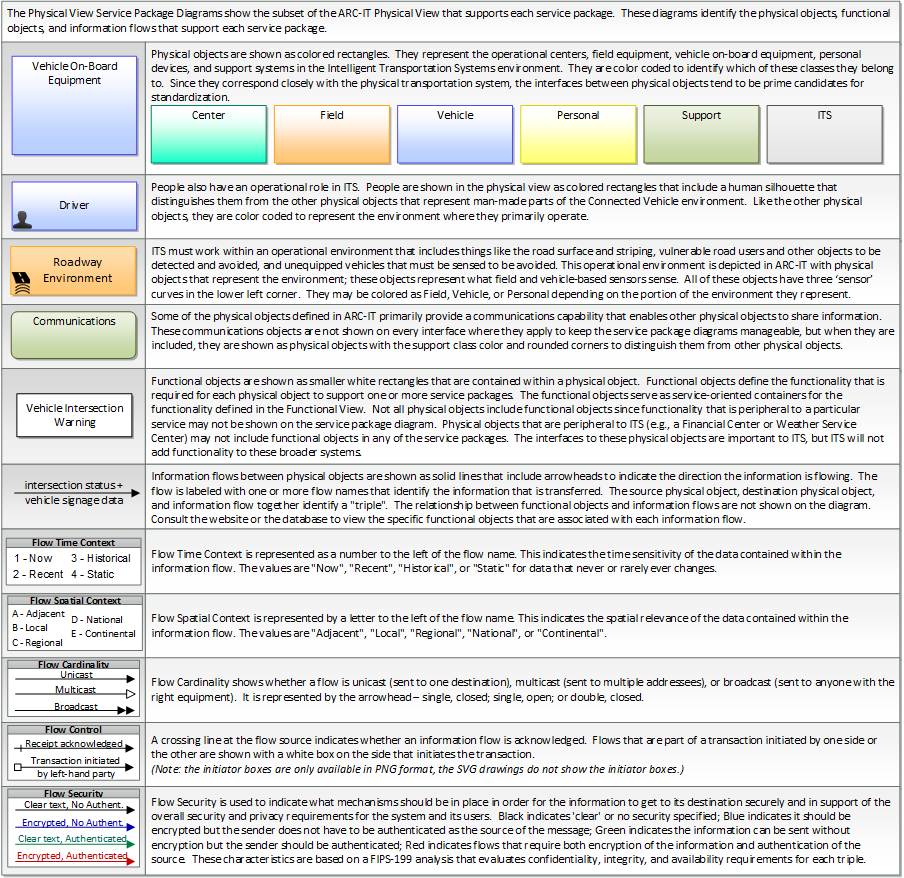
In order to participate in this service package, each physical object should meet or exceed the following security levels.
In order to participate in this service package, each information flow triple should meet or exceed the following security levels.
| Information Flow Security |
| Source |
Destination |
Information Flow |
Confidentiality |
Integrity |
Availability |
| Basis |
Basis |
Basis |
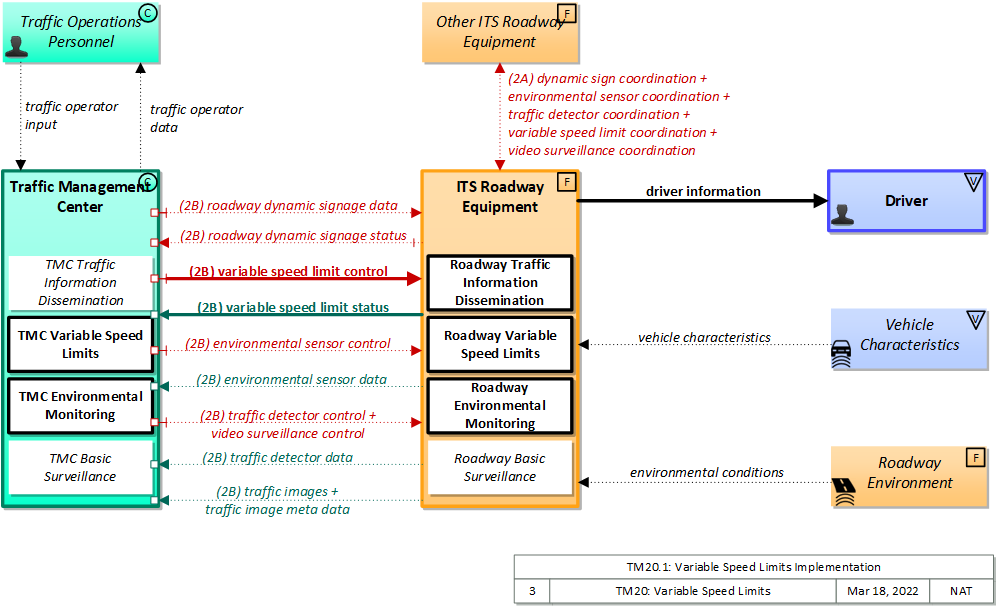
| ITS Roadway Equipment |
Driver |
driver information |
Not Applicable |
High |
Moderate |
| This data is sent to all drivers and is also directly observable, by design. |
This is the primary signal trusted by the driver to decide whether to go through the intersection and what speed to go through the intersection at; if it’s wrong, accidents could happen. |
If the lights are out you have to get a policeman to direct traffic – expensive and inefficient and may cause a cascading effect due to lack of coordination with other intersections. |
| ITS Roadway Equipment |
Other ITS Roadway Equipment |
dynamic sign coordination |
Moderate |
Moderate |
Moderate |
| Any control flow has some confidentiality requirement, as observation of the flow may enable an attacker to analyze and learn how to assume control. MODERATE for most flows as the potential damage is likely contained, though anything that could have a significant safety impact may be assigned HIGH. |
Since this directly impacts device control, we consider it the same as a control flow. Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. |
Since this directly impacts device control, we consider it the same as a control flow. Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. |
| ITS Roadway Equipment |
Other ITS Roadway Equipment |
environmental sensor coordination |
Moderate |
Moderate |
Low |
| Any control flow has some confidentiality requirement, as observation of the flow may enable an attacker to analyze and learn how to assume control. MODERATE for most flows as the potential damage is likely contained, though anything that could have a significant safety impact may be assigned HIGH. |
Since this directly impacts device control, we consider it the same as a control flow. Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. |
Since this directly impacts device control, we consider it the same as a control flow. Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. |
| ITS Roadway Equipment |
Other ITS Roadway Equipment |
traffic detector coordination |
Moderate |
Moderate |
Low |
| Any control flow has some confidentiality requirement, as observation of the flow may enable an attacker to analyze and learn how to assume control. MODERATE for most flows as the potential damage is likely contained, though anything that could have a significant safety impact may be assigned HIGH. |
Since this directly impacts device control, we consider it the same as a control flow. Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. |
Since this directly impacts device control, we consider it the same as a control flow. Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. |
| ITS Roadway Equipment |
Other ITS Roadway Equipment |
variable speed limit coordination |
Moderate |
Moderate |
Moderate |
| Any control flow has some confidentiality requirement, as observation of the flow may enable an attacker to analyze and learn how to assume control. MODERATE for most flows as the potential damage is likely contained, though anything that could have a significant safety impact may be assigned HIGH. |
Since this directly impacts device control, we consider it the same as a control flow. Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. |
Since this directly impacts device control, we consider it the same as a control flow. Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. |
| ITS Roadway Equipment |
Other ITS Roadway Equipment |
video surveillance coordination |
Moderate |
Moderate |
Moderate |
| Any control flow has some confidentiality requirement, as observation of the flow may enable an attacker to analyze and learn how to assume control. MODERATE for most flows as the potential damage is likely contained, though anything that could have a significant safety impact may be assigned HIGH. |
Since this directly impacts device control, we consider it the same as a control flow. Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. |
Since this directly impacts device control, we consider it the same as a control flow. Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. |
| ITS Roadway Equipment |
Traffic Management Center |
environmental sensor data |
Low |
Moderate |
Moderate |
| Little to no impact if this data is observed |
info should be correct to determine safe speeds etc.; DISC: WYO believes this to be HIGH |
Updates are desireable but slightly outdated information will not be catastrophic. |
| ITS Roadway Equipment |
Traffic Management Center |
roadway dynamic signage status |
Moderate |
Moderate |
Moderate |
| Device status information should not be available, as those with criminal intent may use this information toward their own ends. |
Data is intended to feed dissemination channels, either C-ITS messages or DMS or other channels, so it should generally be correct as it is distributed widely and any forgery or corrupted data will have widespread impact. |
Failure of this flow affects traveler information dissemination, the importance of which varies with the data contained in the flow and the scenario. Could be LOW in many instances. |
| ITS Roadway Equipment |
Traffic Management Center |
traffic detector data |
Low |
Moderate |
Moderate |
| No impact if someone sees the data |
Some minimal guarantee of data integrity is necessary for all C-ITS flows. THEA believes this to be LOW.only limited adverse effect if raw/processed traffic detector data is bad/compromised; DISC: WYO believes this to be HIGH |
Only limited adverse effect of info is not timely/readily available, however without this information it will be difficult to perform traffic management activities, thus MODERATE. If not used for management, may be LOW. |
| ITS Roadway Equipment |
Traffic Management Center |
traffic image meta data |
Low |
Moderate |
Moderate |
| Traffic image data is generally intended for public consumption, and in any event is already video captured in the public arena, so this must be LOW. |
While accuracy of this data is important for decision making purposes, applications should be able to cfunction without it. Thus MODERATE generally. |
While accuracy of this data is important for decision making purposes, applications should be able to function without it. Thus MODERATE generally. |
| ITS Roadway Equipment |
Traffic Management Center |
traffic images |
Low |
Moderate |
Low |
| Traffic image data is generally intended for public consumption, and in any event is already video captured in the public arena, so this must be LOW. |
Generally transportation coordination information should be correct between source and destination, or inappropriate actions may be taken. |
While useful, there is no signficant impact if this flow is not available. |
| ITS Roadway Equipment |
Traffic Management Center |
variable speed limit status |
Low |
Moderate |
Moderate |
| This information is directly observable |
The TMC will react based on current status of ITS-RE and thus this information should be trusted. DISC: WYO believes this to be HIGH. |
The information should be available to ensure timely response from TMC |
| Other ITS Roadway Equipment |
ITS Roadway Equipment |
dynamic sign coordination |
Moderate |
Moderate |
Moderate |
| Any control flow has some confidentiality requirement, as observation of the flow may enable an attacker to analyze and learn how to assume control. MODERATE for most flows as the potential damage is likely contained, though anything that could have a significant safety impact may be assigned HIGH. |
Since this directly impacts device control, we consider it the same as a control flow. Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. |
Since this directly impacts device control, we consider it the same as a control flow. Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. |
| Other ITS Roadway Equipment |
ITS Roadway Equipment |
environmental sensor coordination |
Moderate |
Moderate |
Low |
| Any control flow has some confidentiality requirement, as observation of the flow may enable an attacker to analyze and learn how to assume control. MODERATE for most flows as the potential damage is likely contained, though anything that could have a significant safety impact may be assigned HIGH. |
Since this directly impacts device control, we consider it the same as a control flow. Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. |
Since this directly impacts device control, we consider it the same as a control flow. Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. |
| Other ITS Roadway Equipment |
ITS Roadway Equipment |
traffic detector coordination |
Moderate |
Moderate |
Low |
| Any control flow has some confidentiality requirement, as observation of the flow may enable an attacker to analyze and learn how to assume control. MODERATE for most flows as the potential damage is likely contained, though anything that could have a significant safety impact may be assigned HIGH. |
Since this directly impacts device control, we consider it the same as a control flow. Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. |
Since this directly impacts device control, we consider it the same as a control flow. Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. |
| Other ITS Roadway Equipment |
ITS Roadway Equipment |
variable speed limit coordination |
Moderate |
Moderate |
Moderate |
| Any control flow has some confidentiality requirement, as observation of the flow may enable an attacker to analyze and learn how to assume control. MODERATE for most flows as the potential damage is likely contained, though anything that could have a significant safety impact may be assigned HIGH. |
Since this directly impacts device control, we consider it the same as a control flow. Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. |
Since this directly impacts device control, we consider it the same as a control flow. Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. |
| Other ITS Roadway Equipment |
ITS Roadway Equipment |
video surveillance coordination |
Moderate |
Moderate |
Moderate |
| Any control flow has some confidentiality requirement, as observation of the flow may enable an attacker to analyze and learn how to assume control. MODERATE for most flows as the potential damage is likely contained, though anything that could have a significant safety impact may be assigned HIGH. |
Since this directly impacts device control, we consider it the same as a control flow. Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. |
Since this directly impacts device control, we consider it the same as a control flow. Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. |
| Roadway Environment |
ITS Roadway Equipment |
environmental conditions |
Not Applicable |
Low |
Low |
| Sensor-based information flows by definition have no confidentiality concerns. |
While typically security concerns related to sensing ignored, if considered this would be LOW, as the obfuscation or failure of any given environmental sensor is likely to be overcome by the mass of data necessary to draw environmental concluisions. |
While typically security concerns related to sensing ignored, if considered this would be LOW, as the obfuscation or failure of any given environmental sensor is likely to be overcome by the mass of data necessary to draw environmental concluisions. |
| Traffic Management Center |
ITS Roadway Equipment |
environmental sensor control |
Moderate |
Moderate |
Low |
| Control flows, even for seemingly innocent devices, should be kept confidential to minimize attack vectors. While an individual installation may not be particularly impacted by a cyberattack of its sensor network, another installation might be severely impacted, and different installations are likely to use similar methods, so compromising one leads to compromising all. DISC: THEA, WYO believe this to be LOW: encrypted, authenticated, proprietary; but should not cause severe damage if seen |
Should be accurate and not be tampered with; could enable outside control of traffic sensors but should not cause severe harm, but could cause issues with environmental sensor data received and be detrimental to operations; DISC: WYO believes this may be HIGH for some applications |
Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. From THEAwant updates but delayed information will not be severe; should be able to operate from a previous/default control/config; DISC: WYO believes this to be MODERATE |
| Traffic Management Center |
ITS Roadway Equipment |
roadway dynamic signage data |
Moderate |
Moderate |
Moderate |
| Device control information should not be available, as those with criminal intent may use this information toward their own ends. |
Data is intended to feed dissemination channels, either C-ITS messages or DMS or other channels, so it should generally be correct as it is distributed widely and any forgery or corrupted data will have widespread impact. |
Occasional outages of this flow will delay dissemination of the data to travelers (the eventual end user) which could have significant impacts on travel, both safety and mobility impacts. |
| Traffic Management Center |
ITS Roadway Equipment |
traffic detector control |
Moderate |
Moderate |
Low |
| Control flows, even for seemingly innocent devices, should be kept confidential to minimize attack vectors. While an individual installation may not be particularly impacted by a cyberattack of its sensor network, another installation might be severely impacted, and different installations are likely to use similar methods, so compromising one leads to compromising all. DISC: THEA, WYO believe this to be LOW: encrypted, authenticated, proprietary; but should not cause severe damage if seen |
Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH.. From THEA: should be accurate and not be tampered with; could enable outside control of traffic sensors but should not cause severe harm, but could cause issues with traffic sensor data received and be detrimental to operations |
Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH.. From THEA: want updates but delayed information will not be severe; should be able to operate from a previous/default control/config. DISC: WYO believes this to be MODERATE |
| Traffic Management Center |
ITS Roadway Equipment |
variable speed limit control |
Moderate |
High |
Moderate |
| Control flows, even for seemingly innocent devices, should be kept confidential to minimize attack vectors. While an individual installation may not be particularly impacted by a cyberattack of its sensor network, another installation might be severely impacted, and different installations are likely to use similar methods, so compromising one leads to compromising all.. DISC: WYO believes this to be LOW or MODERATE depending on the application. NYC believes it to be LOW, as this information is directly observable. |
Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. From NYC: The information sent from TMC directly affect the ITS-RE speed “announcement”. |
NYC: The ITS-RE can work accordingly or in fail-safe if information is not available. WYO believes this to be MODERATE. Given the impacts for WYO scnearios, defaulted to MODERATE. |
| Traffic Management Center |
ITS Roadway Equipment |
video surveillance control |
Moderate |
Moderate |
Moderate |
| Control flows, even for seemingly innocent devices, should be kept confidential to minimize attack vectors. While an individual installation may not be particularly impacted by a cyberattack of its sensor network, another installation might be severely impacted, and different installations are likely to use similar methods, so compromising one leads to compromising all. |
Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. |
Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. |
| Traffic Management Center |
Traffic Operations Personnel |
traffic operator data |
Moderate |
Moderate |
Moderate |
| Backoffice operations flows should have minimal protection from casual viewing, as otherwise imposters could gain illicit control or information that should not be generally available. |
Information presented to backoffice system operators must be consistent or the operator may perform actions that are not appropriate to the real situation. |
The backoffice system operator should have access to system operation. If this interface is down then control is effectively lost, as without feedback from the system the operator has no way of knowing what is the correct action to take. |
| Traffic Operations Personnel |
Traffic Management Center |
traffic operator input |
Moderate |
High |
High |
| Backoffice operations flows should have minimal protection from casual viewing, as otherwise imposters could gain illicit control or information that should not be generally available. |
Backoffice operations flows should generally be correct and available as these are the primary interface between operators and system. |
Backoffice operations flows should generally be correct and available as these are the primary interface between operators and system. |
| Vehicle Characteristics |
ITS Roadway Equipment |
vehicle characteristics |
|
|
|
|
|
|