In order to participate in this service package, each physical object should meet or exceed the following security levels.
In order to participate in this service package, each information flow triple should meet or exceed the following security levels.
| Information Flow Security |
| Source |
Destination |
Information Flow |
Confidentiality |
Integrity |
Availability |
| Basis |
Basis |
Basis |
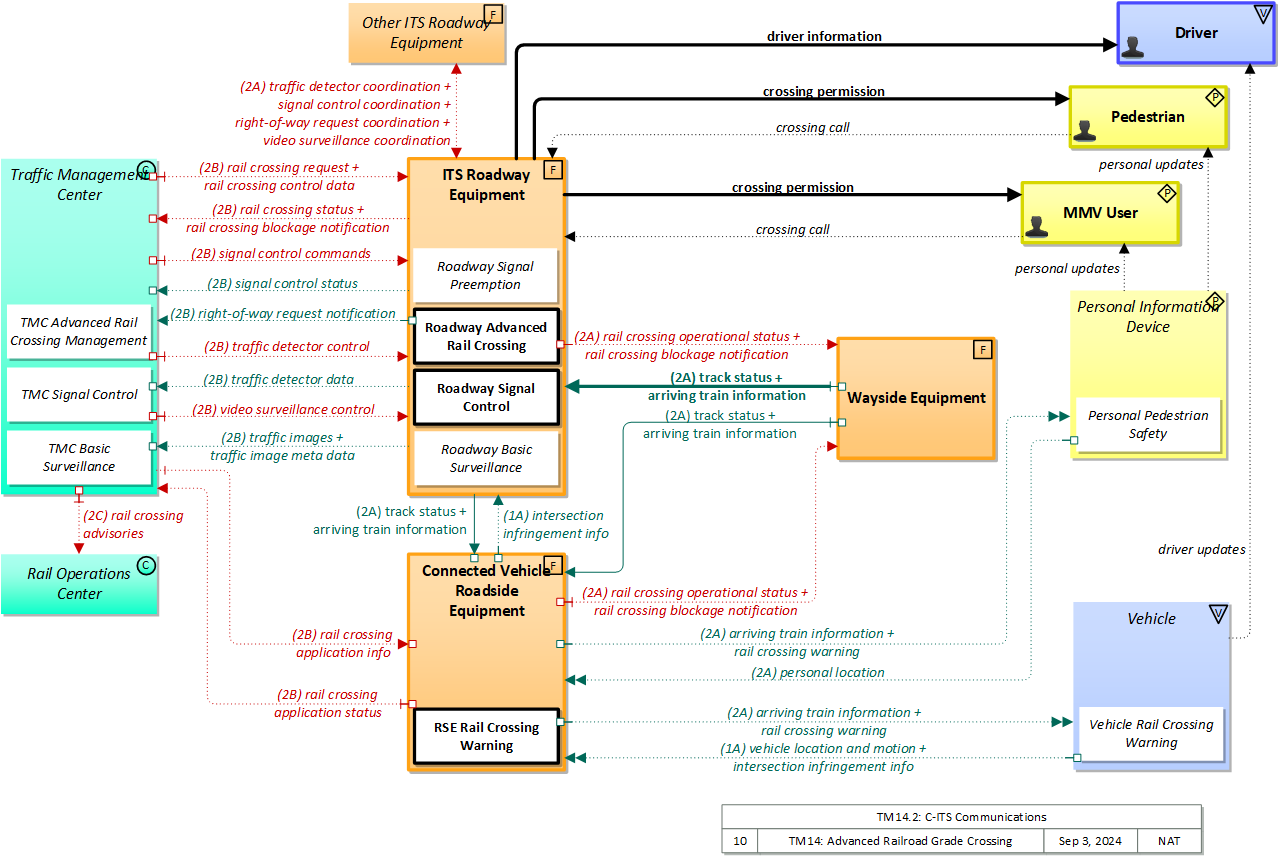
| Connected Vehicle Roadside Equipment |
ITS Roadway Equipment |
intersection infringement info |
Low |
High |
Moderate |
| This data is also transmitted to those in the local vicinity via broadcast. |
This message is an indication of a potential hazard and should not be easy to forge. False messages here may lead to confusion that causes a traffic accident. |
This message is an indication of a potential hazard. If it isn’t received it increases the risk to other road users. If a vehicle is infringing on an intersection, it must report this. |
| Connected Vehicle Roadside Equipment |
Personal Information Device |
arriving train information |
Not Applicable |
High |
High |
| Trains arriving should be visible, viewable and certainly not concealed. |
This flow forms the basis for providing data that, if incorrect, could lead to a catastrophic mistake. |
This flow forms the basis for providing data that, if incorrect, could lead to a catastrophic mistake. Since this flow can lead to other actions with other effects, HIGH is justifiable. |
| Connected Vehicle Roadside Equipment |
Personal Information Device |
rail crossing warning |
Not Applicable |
High |
Moderate |
| This is directly observable data. |
While there are other mechanisms for receiving this information, this data flow needs to be accurate lest a catastrophic mistake be made. |
While the data is critically important, there are other mechanisms for noting an approaching train (crossing gates, the train itself). |
| Connected Vehicle Roadside Equipment |
Traffic Management Center |
rail crossing application status |
Moderate |
Moderate |
Low |
| This information could be of interest to a malicious individual who is attempting to determine the best way to accomplish a crime. As such it would be best to not make it easily accessible. |
If this is compromised, it could send unnecessary maintenance workers, or cause the appearance of excessive traffic violations, leading to further unnecessary investigation. |
A delay in reporting this may cause a delay in necessary maintenance, but (a) this is not time-critical and (b) there are other channels for reporting malfunctioning. Additionally, there is a message received notification, which means that RSE can ensure that all intersection safety issues are delivered. |
| Connected Vehicle Roadside Equipment |
Vehicle |
arriving train information |
Not Applicable |
High |
Moderate |
| Trains arriving should be visible, viewable and certainly not concealed. |
While there are other mechanisms for receiving this information, this data flow needs to be accurate lest a catastrophic mistake be made. |
While the data is critically important, there are other mechanisms for noting an approaching train (crossing gates, the train itself). |
| Connected Vehicle Roadside Equipment |
Vehicle |
rail crossing warning |
Not Applicable |
High |
Moderate |
| This is directly observable data. |
While there are other mechanisms for receiving this information, this data flow needs to be accurate lest a catastrophic mistake be made. |
While the data is critically important, there are other mechanisms for noting an approaching train (crossing gates, the train itself). |
| Connected Vehicle Roadside Equipment |
Wayside Equipment |
rail crossing blockage notification |
Moderate |
High |
High |
| Contains information that may be predictive of a serious traffic/rail incident. For privacy purposes, this should probably not be advertised. |
Data predictive of potentially catastrophic incident needs to be correct so that appropriate actions are taken. |
This is a high priority to the vehicle blocking the HRI. Impact is not broad, but very severe. Hard to justify a MODERATE given the consequences. |
| Connected Vehicle Roadside Equipment |
Wayside Equipment |
rail crossing operational status |
Moderate |
Moderate |
Moderate |
| This information could be of interest to a malicious individual who is attempting to determine the best way to accomplish a crime. As such it would be best to not make it easily accessible. |
If this is compromised, it could send unnecessary maintenance workers, or suggest actions that are incorrect for the true situation. |
This information is important, but if it is not reported there are other safety systems that should prevent related incidents. The impact of any rail/road intersection is particularly high, but in this case a MODERATE rating can be justified by the alternative mechanisms. |
| ITS Roadway Equipment |
Connected Vehicle Roadside Equipment |
arriving train information |
Not Applicable |
High |
High |
| Trains arriving should be visible, viewable and certainly not concealed. |
This flow is an intermediate to the end user, but may also be used by an intermediary process for some other action. Regardless, it forms the basis for providing data that, if incorrect, could lead to a catastrophic mistake. |
This flow is an intermediate to the end user, but may also be used by an intermediary process for some other action. Regardless, it forms the basis for providing data that, if incorrect, could lead to a catastrophic mistake. Since this flow can lead to other actions with other effects, HIGH is justifiable. |
| ITS Roadway Equipment |
Connected Vehicle Roadside Equipment |
track status |
Low |
High |
High |
| Track status is typically physically viewable information. |
While this can be corroborated visually, the RSE may rely on this information to make safety-related decisions with significant consequences, so the data must be of high quality and readily available. |
While this can be corroborated visually, the RSE may rely on this information to make safety-related decisions with significant consequences, so the data must be of high quality and readily available. |
| ITS Roadway Equipment |
Driver |
driver information |
Not Applicable |
High |
Moderate |
| This data is sent to all drivers and is also directly observable, by design. |
This is the primary signal trusted by the driver to decide whether to go through the intersection and what speed to go through the intersection at; if it’s wrong, accidents could happen. |
If the lights are out you have to get a policeman to direct traffic – expensive and inefficient and may cause a cascading effect due to lack of coordination with other intersections. |
| ITS Roadway Equipment |
MMV User |
crossing permission |
Not Applicable |
High |
Low |
| This data is intentionally transmitted to everyone via a broadcast. |
Although pedestrians have a responsibility to make sure the road is safe before they cross, they may react instinctively to incorrect information and be led to cross at unsafe times if they get incorrect information. Also, if the traffic signals are wrong and an accident happens, the pedestrian involved could sue, causing financial loss and other undesirable outcomes. |
It is easy to tell whether this information flow is available and pedestrians are used to using crosswalks that do not provide this service. |
| ITS Roadway Equipment |
Other ITS Roadway Equipment |
right-of-way request coordination |
Moderate |
Moderate |
Moderate |
| Any control flow has some confidentiality requirement, as observation of the flow may enable an attacker to analyze and learn how to assume control. MODERATE for most flows as the potential damage is likely contained, though anything that could have a significant safety impact may be assigned HIGH. |
Since this directly impacts device control, we consider it the same as a control flow. Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. |
Since this directly impacts device control, we consider it the same as a control flow. Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. |
| ITS Roadway Equipment |
Other ITS Roadway Equipment |
signal control coordination |
Moderate |
Moderate |
Moderate |
| Any control flow has some confidentiality requirement, as observation of the flow may enable an attacker to analyze and learn how to assume control. MODERATE for most flows as the potential damage is likely contained, though anything that could have a significant safety impact may be assigned HIGH. |
Since this directly impacts device control, we consider it the same as a control flow. Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. |
Since this directly impacts device control, we consider it the same as a control flow. Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. |
| ITS Roadway Equipment |
Other ITS Roadway Equipment |
traffic detector coordination |
Moderate |
Moderate |
Low |
| Any control flow has some confidentiality requirement, as observation of the flow may enable an attacker to analyze and learn how to assume control. MODERATE for most flows as the potential damage is likely contained, though anything that could have a significant safety impact may be assigned HIGH. |
Since this directly impacts device control, we consider it the same as a control flow. Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. |
Since this directly impacts device control, we consider it the same as a control flow. Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. |
| ITS Roadway Equipment |
Other ITS Roadway Equipment |
video surveillance coordination |
Moderate |
Moderate |
Moderate |
| Any control flow has some confidentiality requirement, as observation of the flow may enable an attacker to analyze and learn how to assume control. MODERATE for most flows as the potential damage is likely contained, though anything that could have a significant safety impact may be assigned HIGH. |
Since this directly impacts device control, we consider it the same as a control flow. Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. |
Since this directly impacts device control, we consider it the same as a control flow. Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. |
| ITS Roadway Equipment |
Pedestrian |
crossing permission |
Not Applicable |
High |
Low |
| This data is intentionally transmitted to everyone via a broadcast. |
Although pedestrians have a responsibility to make sure the road is safe before they cross, they may react instinctively to incorrect information and be led to cross at unsafe times if they get incorrect information. Also, if the traffic signals are wrong and an accident happens, the pedestrian involved could sue, causing financial loss and other undesirable outcomes. |
It is easy to tell whether this information flow is available and pedestrians are used to using crosswalks that do not provide this service. |
| ITS Roadway Equipment |
Traffic Management Center |
rail crossing blockage notification |
Moderate |
High |
High |
| Contains information that may be predictive of a serious traffic/rail incident. For privacy purposes, this should probably not be advertised. |
Data predictive of potentially catastrophic incident needs to be correct so that appropriate actions are taken. |
This is a high priority to the vehicle blocking the HRI. Impact is not broad, but very severe. Hard to justify a MODERATE given the consequences. |
| ITS Roadway Equipment |
Traffic Management Center |
rail crossing status |
Moderate |
Moderate |
Moderate |
| This information could be of interest to a malicious individual who is attempting to determine the best way to accomplish a crime. As such it would be best to not make it easily accessible. |
If this is compromised, it could send unnecessary maintenance workers, or suggest actions that are incorrect for the true situation. |
This information is important, but if it is not reported there are other safety systems that should prevent related incidents. The impact of any rail/road intersection is particularly high, but in this case a MODERATE rating can be justified by the alternative mechanisms. |
| ITS Roadway Equipment |
Traffic Management Center |
right-of-way request notification |
Low |
Moderate |
Moderate |
| This can be reasonably guessed based on observing the ITS RE’s environment. It is obvious when a bus approaches an intersection. |
Invalid messages could lead to an unauthorized user gaining signal priority at an intersection. This could also be used to delay traffic, which could lead to a financial impact on the community. However, the traffic signal will have controls in place to ensure that it does not display an illegal configuration (such as green in every direction). |
Even if all of the Right-of-way Requests are not passed along from an ITS RE, the intersection will still operate as normal. There are other existing methods to assist a right-of-way requesting vehicle safely traveling through an intersection, such as lights and sirens, which prevent this from being a HIGH. DISC: THEA and NYC believe this to be LOW: "not necessary for the app to work; can cope with not having immediately available data" |
| ITS Roadway Equipment |
Traffic Management Center |
signal control status |
Low |
High |
Moderate |
| The current conditions of an ITS RE are completely observable, by design. |
This influences the TMC response to a right-of-way request. It should be as accurate as the right-of-way request themselves. For some applications (ISIG) this need only be moderate. Per THEA: info needs to be accurate and should not be tampered to enable effective monitoring and control by the TMC. DISC: THEA believes this to be MODERATE: "info needs to be accurate and should not be tampered to enable effective monitoring and control by the TMC; should be as accurate as the right of way request". NYC:TMC doesn’t play an active role in this application, i.e. even if the information contained in this flow were incorrect, it is unlikely to affect the outcome of this application one way or the other. On some applications NYC has this MODERATE though. RES: This value can obviously change a lot depending on the application context. |
The TMC will need the current status of the ITS RE in order to make an educated decision. If it is unavailable, the system is unable to operate. However, a few missed messages will not have a catastrophic impact. From NYC: TMC doesn’t play an active role in this application, i.e. even if it is unavailable, it is unlikely to affect the outcome of this application one way or the other. RES: This value can change a lot depending on the application context. |
| ITS Roadway Equipment |
Traffic Management Center |
traffic detector data |
Low |
Moderate |
Moderate |
| No impact if someone sees the data |
Some minimal guarantee of data integrity is necessary for all C-ITS flows. THEA believes this to be LOW.only limited adverse effect if raw/processed traffic detector data is bad/compromised; DISC: WYO believes this to be HIGH |
Only limited adverse effect of info is not timely/readily available, however without this information it will be difficult to perform traffic management activities, thus MODERATE. If not used for management, may be LOW. |
| ITS Roadway Equipment |
Traffic Management Center |
traffic image meta data |
Low |
Moderate |
Moderate |
| Traffic image data is generally intended for public consumption, and in any event is already video captured in the public arena, so this must be LOW. |
While accuracy of this data is important for decision making purposes, applications should be able to cfunction without it. Thus MODERATE generally. |
While accuracy of this data is important for decision making purposes, applications should be able to function without it. Thus MODERATE generally. |
| ITS Roadway Equipment |
Traffic Management Center |
traffic images |
Low |
Moderate |
Low |
| Traffic image data is generally intended for public consumption, and in any event is already video captured in the public arena, so this must be LOW. |
Generally transportation coordination information should be correct between source and destination, or inappropriate actions may be taken. |
While useful, there is no signficant impact if this flow is not available. |
| ITS Roadway Equipment |
Wayside Equipment |
rail crossing blockage notification |
Moderate |
High |
High |
| Contains information that may be predictive of a serious traffic/rail incident. For privacy purposes, this should probably not be advertised. |
Data predictive of potentially catastrophic incident needs to be correct so that appropriate actions are taken. |
This is a high priority to the vehicle blocking the HRI. Impact is not broad, but very severe. Hard to justify a MODERATE given the consequences. |
| ITS Roadway Equipment |
Wayside Equipment |
rail crossing operational status |
Moderate |
Moderate |
Moderate |
| This information could be of interest to a malicious individual who is attempting to determine the best way to accomplish a crime. As such it would be best to not make it easily accessible. |
If this is compromised, it could send unnecessary maintenance workers, or suggest actions that are incorrect for the true situation. |
This information is important, but if it is not reported there are other safety systems that should prevent related incidents. The impact of any rail/road intersection is particularly high, but in this case a MODERATE rating can be justified by the alternative mechanisms. |
| MMV User |
ITS Roadway Equipment |
crossing call |
Not Applicable |
High |
Low |
| The "Not Applicable" group includes information flows that do not actually carry information; for example, flows that represent the physical environment. |
Although pedestrians have a responsibility to make sure the road is safe before they cross, and should ensure that they are detected by pedestrian detection systems, they may not always be detected and be led to cross at unsafe times if the ITS RE obtains incorrect information. |
It is easy to tell whether this information flow is available and pedestrians are used to using crosswalks that do not provide this service. |
| Other ITS Roadway Equipment |
ITS Roadway Equipment |
right-of-way request coordination |
Moderate |
Moderate |
Moderate |
| Any control flow has some confidentiality requirement, as observation of the flow may enable an attacker to analyze and learn how to assume control. MODERATE for most flows as the potential damage is likely contained, though anything that could have a significant safety impact may be assigned HIGH. |
Since this directly impacts device control, we consider it the same as a control flow. Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. |
Since this directly impacts device control, we consider it the same as a control flow. Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. |
| Other ITS Roadway Equipment |
ITS Roadway Equipment |
signal control coordination |
Moderate |
Moderate |
Moderate |
| Any control flow has some confidentiality requirement, as observation of the flow may enable an attacker to analyze and learn how to assume control. MODERATE for most flows as the potential damage is likely contained, though anything that could have a significant safety impact may be assigned HIGH. |
Since this directly impacts device control, we consider it the same as a control flow. Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. |
Since this directly impacts device control, we consider it the same as a control flow. Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. |
| Other ITS Roadway Equipment |
ITS Roadway Equipment |
traffic detector coordination |
Moderate |
Moderate |
Low |
| Any control flow has some confidentiality requirement, as observation of the flow may enable an attacker to analyze and learn how to assume control. MODERATE for most flows as the potential damage is likely contained, though anything that could have a significant safety impact may be assigned HIGH. |
Since this directly impacts device control, we consider it the same as a control flow. Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. |
Since this directly impacts device control, we consider it the same as a control flow. Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. |
| Other ITS Roadway Equipment |
ITS Roadway Equipment |
video surveillance coordination |
Moderate |
Moderate |
Moderate |
| Any control flow has some confidentiality requirement, as observation of the flow may enable an attacker to analyze and learn how to assume control. MODERATE for most flows as the potential damage is likely contained, though anything that could have a significant safety impact may be assigned HIGH. |
Since this directly impacts device control, we consider it the same as a control flow. Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. |
Since this directly impacts device control, we consider it the same as a control flow. Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. |
| Pedestrian |
ITS Roadway Equipment |
crossing call |
Not Applicable |
High |
Low |
| The "Not Applicable" group includes information flows that do not actually carry information; for example, flows that represent the physical environment. |
Although pedestrians have a responsibility to make sure the road is safe before they cross, and should ensure that they are detected by pedestrian detection systems, they may not always be detected and be led to cross at unsafe times if the ITS RE obtains incorrect information. |
It is easy to tell whether this information flow is available and pedestrians are used to using crosswalks that do not provide this service. |
| Personal Information Device |
Connected Vehicle Roadside Equipment |
personal location |
Not Applicable |
High |
Moderate |
| This data is intentionally transmitted to everyone via a broadcast. It can also be determined via other visual indicators. |
An incorrect location message could lead to a false warning or lack of warning. A lack of warning can have obvious catastrophic consequences, while a false warning could lead to users ignoring warnings due to perceived inaccuracy. Given that this triple may apply to highly dynamic environments (such as work zones), its accuracy is paramount, and thus if sent, must have HIGH integrity. |
There are other visual indicators about the geofenced areas. PID users in dynamic environments (incident and work zones) should know when they are leaving a geofenced area. As long as they remain in the geofenced area, this information is not as necessary. Not all pedestrians will carry a personal information device, and the system should be able to operate without this information. |
| Personal Information Device |
MMV User |
personal updates |
Not Applicable |
Moderate |
Moderate |
| This data is informing the pedestrian about the safety of the intersections. It should not contain anything sensitive, and does not matter if another person can observe it. |
This is the information that is presented to the individual. If they receive incorrect information, they may act in an unsafe manner. However, there are other indicators that would alert them to any hazards, such as an oncoming vehicle or crossing safety lights. |
If this information is not made available to the pedestrian, then the system has not operated correctly. |
| Personal Information Device |
Pedestrian |
personal updates |
Not Applicable |
Moderate |
Moderate |
| This data is informing the pedestrian about the safety of the intersections. It should not contain anything sensitive, and does not matter if another person can observe it. |
This is the information that is presented to the individual. If they receive incorrect information, they may act in an unsafe manner. However, there are other indicators that would alert them to any hazards, such as an oncoming vehicle or crossing safety lights. |
If this information is not made available to the pedestrian, then the system has not operated correctly. |
| Traffic Management Center |
Connected Vehicle Roadside Equipment |
rail crossing application info |
Moderate |
Moderate |
Low |
| This information could be of interest to a malicious individual who is attempting to determine the best way to accomplish a crime. As such it would be best to not make it easily accessible. |
If this is compromised, it could send unnecessary maintenance workers, or cause the appearance of excessive traffic violations, leading to further unnecessary investigation. |
A delay in reporting this may cause a delay in necessary maintenance, but (a) this is not time-critical and (b) there are other channels for reporting malfunctioning. Additionally, there is a message received notification, which means that RSE can ensure that all intersection safety issues are delivered. |
| Traffic Management Center |
ITS Roadway Equipment |
rail crossing control data |
Moderate |
High |
Moderate |
| Control flows, even for seemingly innocent devices, should be kept confidential to minimize attack vectors. While an individual installation may not be particularly impacted by a cyberattack of its sensor network, another installation might be severely impacted, and different installations are likely to use similar methods, so compromising one leads to compromising all. |
Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. |
Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. |
| Traffic Management Center |
ITS Roadway Equipment |
rail crossing request |
Moderate |
Moderate |
Moderate |
| This information could be of interest to a malicious individual who is attempting to determine the best way to accomplish a crime. As such it would be best to not make it easily accessible. |
If this is compromised, it could send unnecessary maintenance workers, or suggest actions that are incorrect for the true situation. |
This information is important, but if it is not reported there are other safety systems that should prevent related incidents. The impact of any rail/road intersection is particularly high, but in this case a MODERATE rating can be justified by the alternative mechanisms. |
| Traffic Management Center |
ITS Roadway Equipment |
signal control commands |
Moderate |
High |
Moderate |
| Control flows, even for seemingly innocent devices, should be kept confidential to minimize attack vectors. While an individual installation may not be particularly impacted by a cyberattack of its sensor network, another installation might be severely impacted, and different installations are likely to use similar methods, so compromising one leads to compromising all. DISC: NYC believes this to be LOW: "The result of this will be directly observable." |
Invalid messages could lead to an unauthorized user gaining control of an intersection. This could also be used to bring traffic to a standstill, which could lead to a large financial impact on the community. DISC: NYC believes this to be MODERATE: The signal timing is critical to the intersection operation; incorrect signal timing can lead to significant congestion and unreliable operation; while unsafe operation is controlled by the cabinet monitoring system, attackers could “freeze” the signal or call a preemption. RES: This will vary depending on the application and implementation. |
These messages are important to help with preemption and signal priority applications. Without them, these applications mayl not work. However, if these signals are not received, the ITS RE will continue to function using its default configuration. The TMC should have an acknowledgement of the receipt of a message. DISC: NYC blieves this to be LOW: TMC doesn’t play an active role in this application, i.e. even if it is unavailable, it is unlikely to affect the outcome of this application one way or the other.
RES: This will vary depending on the application and implementation. |
| Traffic Management Center |
ITS Roadway Equipment |
traffic detector control |
Moderate |
Moderate |
Low |
| Control flows, even for seemingly innocent devices, should be kept confidential to minimize attack vectors. While an individual installation may not be particularly impacted by a cyberattack of its sensor network, another installation might be severely impacted, and different installations are likely to use similar methods, so compromising one leads to compromising all. DISC: THEA, WYO believe this to be LOW: encrypted, authenticated, proprietary; but should not cause severe damage if seen |
Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH.. From THEA: should be accurate and not be tampered with; could enable outside control of traffic sensors but should not cause severe harm, but could cause issues with traffic sensor data received and be detrimental to operations |
Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH.. From THEA: want updates but delayed information will not be severe; should be able to operate from a previous/default control/config. DISC: WYO believes this to be MODERATE |
| Traffic Management Center |
ITS Roadway Equipment |
video surveillance control |
Moderate |
Moderate |
Moderate |
| Control flows, even for seemingly innocent devices, should be kept confidential to minimize attack vectors. While an individual installation may not be particularly impacted by a cyberattack of its sensor network, another installation might be severely impacted, and different installations are likely to use similar methods, so compromising one leads to compromising all. |
Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. |
Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. |
| Traffic Management Center |
Rail Operations Center |
rail crossing advisories |
Moderate |
Moderate |
Moderate |
| May contain sensitive information about the highway-rail intersection area. If intercepted by a third party, could be used to embarras the relevant stakeholders, or as contributing information toward target selection (if for example a piece of monitoring equipment was listed as non-functional). |
This will trigger maintenance activity, so it must be correct or such activities will not be properly scheduled and resources suboptimally assgned. If unavailable or modified, may negatively contribute to mobility and safety. |
This will trigger maintenance activity, so it must be correct or such activities will not be properly scheduled and resources suboptimally assgned. If unavailable or modified, may negatively contribute to mobility and safety. |
| Vehicle |
Connected Vehicle Roadside Equipment |
intersection infringement info |
Low |
High |
Moderate |
| This data is intentionally transmitted to everyone via a broadcast. It can also be determined via other visual indicators. |
This message is an indication of a potential hazard and should not be easy to forge. False messages here may lead to confusion that causes a traffic accident. |
This message is an indication of a potential hazard. If it isn’t received it increases the risk to other road users. If a vehicle is infringing on an intersection, it must report this. |
| Vehicle |
Connected Vehicle Roadside Equipment |
vehicle location and motion |
Not Applicable |
High |
Moderate |
| This data is intentionally transmitted to everyone via a broadcast. Much of its information content can also be determined via other visual indicators |
Incorrect information could lead to the system not operating properly. If the system does not properly know where the vehicle is, it cannot make an accurate decision about whether there is going to be a pedestrian in the crosswalk that the vehicle is approaching. This can have a safety impact.; DISC: NYC believes this to be MODERATE |
This data is required for the system to operate properly. If this data is not available, the system cannot give accurate warning information. |
| Vehicle |
Driver |
driver updates |
Not Applicable |
Moderate |
Moderate |
| This data is informing the driver about the safety of a nearby area. It should not contain anything sensitive, and does not matter if another person can observe it. |
This is the information that is presented to the driver. If they receive incorrect information, they may act in an unsafe manner. However, there are other indicators that would alert them to any hazards, such as an oncoming vehicle or crossing safety lights. |
If this information is not made available to the driver, then the system has not operated correctly. |
| Wayside Equipment |
Connected Vehicle Roadside Equipment |
arriving train information |
Not Applicable |
High |
High |
| Trains arriving should be visible, viewable and certainly not concealed. |
This flow is an intermediate to the end user, but may also be used by an intermediary process for some other action. Regardless, it forms the basis for providing data that, if incorrect, could lead to a catastrophic mistake. |
This flow is an intermediate to the end user, but may also be used by an intermediary process for some other action. Regardless, it forms the basis for providing data that, if incorrect, could lead to a catastrophic mistake. Since this flow can lead to other actions with other effects, HIGH is justifiable. |
| Wayside Equipment |
Connected Vehicle Roadside Equipment |
track status |
Low |
Moderate |
Moderate |
| Track status is typically physically viewable information. |
This information is important, but if it is incorrecct there are other safety systems that should prevent related incidents. The impact of any rail/road intersection is particularly high, but in this case a MODERATE rating can be justified by the alternative mechanisms. |
This information is important, but if it is not reported there are other safety systems that should prevent related incidents. The impact of any rail/road intersection is particularly high, but in this case a MODERATE rating can be justified by the alternative mechanisms. |
| Wayside Equipment |
ITS Roadway Equipment |
arriving train information |
Not Applicable |
High |
High |
| Trains arriving should be visible, viewable and certainly not concealed. |
This flow is an intermediate to the end user, but may also be used by an intermediary process for some other action. Regardless, it forms the basis for providing data that, if incorrect, could lead to a catastrophic mistake. |
This flow is an intermediate to the end user, but may also be used by an intermediary process for some other action. Regardless, it forms the basis for providing data that, if incorrect, could lead to a catastrophic mistake. Since this flow can lead to other actions with other effects, HIGH is justifiable. |
| Wayside Equipment |
ITS Roadway Equipment |
track status |
Low |
Moderate |
Moderate |
| Track status is typically physically viewable information. |
This information is important, but if it is incorrect there are other safety systems that should prevent related incidents. The impact of any rail/road intersection is particularly high, but in this case a MODERATE rating can be justified by the alternative mechanisms. |
This information is important, but if it is not reported there are other safety systems that should prevent related incidents. The impact of any rail/road intersection is particularly high, but in this case a MODERATE rating can be justified by the alternative mechanisms. |