In order to participate in this service package, each physical object should meet or exceed the following security levels.
In order to participate in this service package, each information flow triple should meet or exceed the following security levels.
| Information Flow Security |
| Source |
Destination |
Information Flow |
Confidentiality |
Integrity |
Availability |
| Basis |
Basis |
Basis |
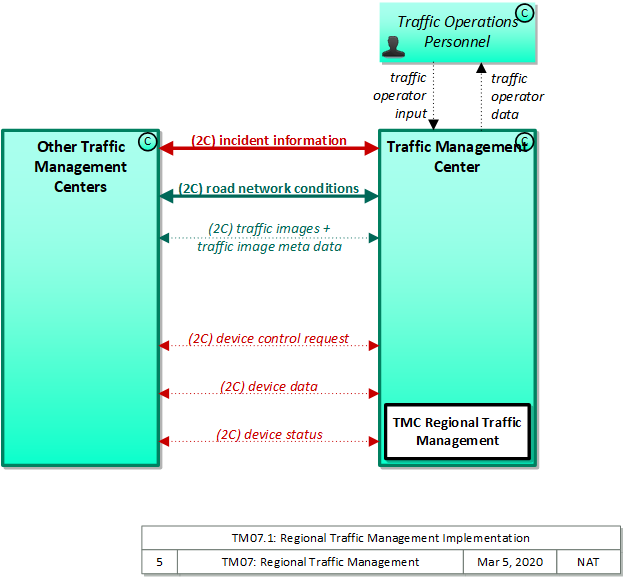
| Other Traffic Management Centers |
Traffic Management Center |
device control request |
Moderate |
High |
Moderate |
| Control flows, even for seemingly innocent devices, should be kept confidential to minimize attack vectors. While an individual installation may not be particularly impacted by a cyberattack of its sensor network, another installation might be severely impacted, and different installations are likely to use similar methods, so compromising one leads to compromising all. |
Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. |
There should be multiple mechanisms for this information to arrive at the end recipient. If this is the only mechanism, should be raised to MODERATE. |
| Other Traffic Management Centers |
Traffic Management Center |
device data |
Moderate |
Moderate |
Low |
| Contains device identity, location and capabilities. If this information were available to a cybercriminal, it may make his task easier and compromise the systems involved. |
If this is corrupted, the other center will not properly understand the device capabilities and not properly leverage them, costing performance. |
Probably does not need to be updated often. |
| Other Traffic Management Centers |
Traffic Management Center |
device status |
Moderate |
Moderate |
Moderate |
| Device status information should be concealed, as an unauthorized observer could use this to reverse engineer device control systems. |
Device status information needs to be available and correct, or the controlling system may take inappropriate maintenance action, costing time and money. |
Device status information needs to be available and correct, or the controlling system may take inappropriate maintenance action, costing time and money. |
| Other Traffic Management Centers |
Traffic Management Center |
incident information |
High |
Moderate |
Moderate |
| This data contains all of the information regarding the incident. This could include personal information regarding persons involved in the incident. It could also include sensitive information regarding special events or closures. |
Incident response and planning details need to be accurate or incorrect decisions or expectations may result, having a significant impact on mobility and operations. |
Real-time access to incident response information is important to management of transportation assets and incident response assets, but does not warrant 'High' because this flow is about adjacent centers, and has no direct impact on the response being given. |
| Other Traffic Management Centers |
Traffic Management Center |
road network conditions |
Low |
Moderate |
Moderate |
| No harm should come from seeing this data, as it is eventually intended for public consumption. |
While accuracy of this data is important for decision making purposes, applications should be able to corroborate the data in many instances. Thus MODERATE generally. |
Depends on the application; if mobility decisions that affect large numbers of travelers are made based on this data, then it is MODERATE. In more modest circumstances, it may be LOW. |
| Other Traffic Management Centers |
Traffic Management Center |
traffic image meta data |
Low |
Moderate |
Moderate |
| Traffic image data is generally intended for public consumption, and in any event is already video captured in the public arena, so this must be LOW. |
While accuracy of this data is important for decision making purposes, applications should be able to cfunction without it. Thus MODERATE generally. |
While accuracy of this data is important for decision making purposes, applications should be able to function without it. Thus MODERATE generally. |
| Other Traffic Management Centers |
Traffic Management Center |
traffic images |
Low |
Moderate |
Low |
| Traffic image data is generally intended for public consumption, and in any event is already video captured in the public arena, so this must be LOW. |
Generally transportation coordination information should be correct between source and destination, or inappropriate actions may be taken. |
While useful, there is no signficant impact if this flow is not available. |
| Traffic Management Center |
Other Traffic Management Centers |
device control request |
Moderate |
High |
Moderate |
| Control flows, even for seemingly innocent devices, should be kept confidential to minimize attack vectors. While an individual installation may not be particularly impacted by a cyberattack of its sensor network, another installation might be severely impacted, and different installations are likely to use similar methods, so compromising one leads to compromising all. |
Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. |
There should be multiple mechanisms for this information to arrive at the end recipient. If this is the only mechanism, should be raised to MODERATE. |
| Traffic Management Center |
Other Traffic Management Centers |
device data |
Moderate |
Moderate |
Low |
| Contains device identity, location and capabilities. If this information were available to a cybercriminal, it may make his task easier and compromise the systems involved. |
info needs to be accurate and should not be tampered but should be able to cope with some bad data; includes inventory data which could lead to loss of assets if compromised |
data should be timely and readily available, but should not have limited consequences if not |
| Traffic Management Center |
Other Traffic Management Centers |
device status |
Moderate |
Moderate |
Low |
| Device status information should be concealed, as an unauthorized observer could use this to reverse engineer device control systems. |
info needs to be accurate and should not be tampered but should be able to cope with some bad data' could delay maintenance actions or waste resources checking devices that are actually in good status |
status infor should be timely and readily available, but should have very limited consequences if not |
| Traffic Management Center |
Other Traffic Management Centers |
incident information |
High |
Moderate |
Moderate |
| This data contains all of the information regarding the incident. This could include personal information regarding persons involved in the incident. It could also include sensitive information regarding special events or closures. |
Minor discrepancies in this data should not have a catastrophic effect, but it should be reasonably controlled and accurate. |
A few missed messages should not have a significant effect. However, most messages should make it through and the TMC should be able to know if the EMC has received a message. |
| Traffic Management Center |
Other Traffic Management Centers |
road network conditions |
Low |
Moderate |
Moderate |
| encrypted; but no harm should come from seeing this data |
info needs to be accurate and should not be tampered but should be able to cope with some bad data; should be able to confirm conditions by other mechanisms |
condition info should be timely and readily available so that TMCs are aware of current traffic info, conditions, restrictions, etc. but should not have severe/catastrophic consequences if not |
| Traffic Management Center |
Other Traffic Management Centers |
traffic image meta data |
Low |
Moderate |
Moderate |
| Traffic image data is generally intended for public consumption, and in any event is already video captured in the public arena, so this must be LOW. |
While accuracy of this data is important for decision making purposes, applications should be able to cfunction without it. Thus MODERATE generally. |
While accuracy of this data is important for decision making purposes, applications should be able to function without it. Thus MODERATE generally. |
| Traffic Management Center |
Other Traffic Management Centers |
traffic images |
Low |
Moderate |
Moderate |
| Traffic image data is generally intended for public consumption, and in any event is already video captured in the public arena, so this must be LOW. |
While accuracy of this data is important for decision making purposes, applications should be able to cfunction without it. Thus MODERATE generally. |
While accuracy of this data is important for decision making purposes, applications should be able to cfunction without it. Thus MODERATE generally. |
| Traffic Management Center |
Traffic Operations Personnel |
traffic operator data |
Moderate |
Moderate |
Moderate |
| Backoffice operations flows should have minimal protection from casual viewing, as otherwise imposters could gain illicit control or information that should not be generally available. |
Information presented to backoffice system operators must be consistent or the operator may perform actions that are not appropriate to the real situation. |
The backoffice system operator should have access to system operation. If this interface is down then control is effectively lost, as without feedback from the system the operator has no way of knowing what is the correct action to take. |
| Traffic Operations Personnel |
Traffic Management Center |
traffic operator input |
Moderate |
High |
High |
| Backoffice operations flows should have minimal protection from casual viewing, as otherwise imposters could gain illicit control or information that should not be generally available. |
Backoffice operations flows should generally be correct and available as these are the primary interface between operators and system. |
Backoffice operations flows should generally be correct and available as these are the primary interface between operators and system. |